Candyhouse Serial Console
If you reboot your router after setting mainlineLinux=yes, but before flashing with a Candyhouse uImage, you’ll find yourself with a bricked router since both the backdoored SSA and the original stock SSA require mainlineLinux=no to boot.
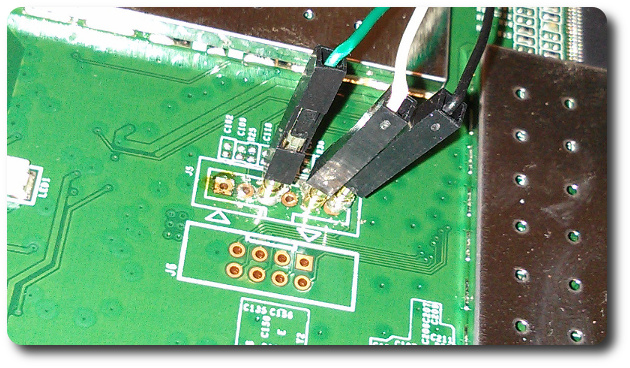
The only way to get out of this situation is to attach some pins to the J5 header and hook into the serial console. You can use any terminal software you like, but personally I prefer gtkterm. The folks at Cisco were nice enough to use the default 8,N,1, so you don’t have to do much configuration.
You will need to grant your user access to /dev/ttyUSB0 (or whatever TTY you use) being that this permission is not granted by default.
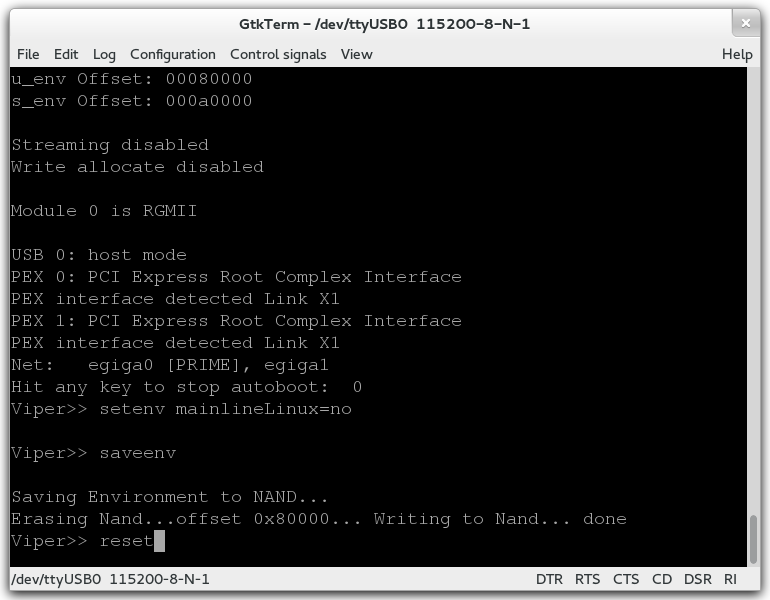
Once you’ve got permissions sorted out, boot the router and repeatedly hit the spacebar in your terminal – you’ll eventually stop the autoboot and get a Viper>> prompt. From there, you just setenv mainlineLinux=no, saveenv, and reset to boot back into the stock or backdoored firmware.
 YouTube!
YouTube!